This post is stolen/copied/inspired from the post by Royce Davis. He posted the awesome original post here on Pentest Geek. I am just taking the hack forward using Nishang and powershell for doing nasty things.
After reading that post I quickly downloaded Jenkins and set it up in my lab. Royce used below code to execute commands on the Jenkins Server.
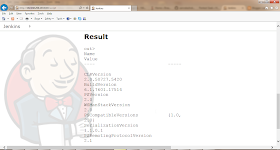
Lets see the version of powershell on the server by using def proc = 'powershell.exe $psversiontable'.execute() in the above code.
And the result is.
Version 2.0. So we can run powershell cmdlets and other commands. Perfect!
Now lets use powershell one-liner downloader to execute different scripts from Nishang on the Jenkins Server.
To execute the scripts we have to append cmd /c to the powershell command. So, for example, to execute Firebuster from Nishang the code becomes
We can also use encoded scripts. Using Invoke-Encode in Nishang, lets encode Get-Information and execute it.
And the output
What's an exploitation without a meterpreter? So lets use the powershell meterpreter payload generated using msf.
And we have a meterpreter session !
So, the conclusion is, whenever and wherever you are able to execute commands on a Windows machine, try to execute powershell commands and you would be happily surprised.
Nishang could be found here: https://github.com/samratashok/nishang
Enjoy!
After reading that post I quickly downloaded Jenkins and set it up in my lab. Royce used below code to execute commands on the Jenkins Server.
Lets see the version of powershell on the server by using def proc = 'powershell.exe $psversiontable'.execute() in the above code.
And the result is.
Version 2.0. So we can run powershell cmdlets and other commands. Perfect!
Now lets use powershell one-liner downloader to execute different scripts from Nishang on the Jenkins Server.
To execute the scripts we have to append cmd /c to the powershell command. So, for example, to execute Firebuster from Nishang the code becomes
We can also use encoded scripts. Using Invoke-Encode in Nishang, lets encode Get-Information and execute it.
So, the conclusion is, whenever and wherever you are able to execute commands on a Windows machine, try to execute powershell commands and you would be happily surprised.
Nishang could be found here: https://github.com/samratashok/nishang
Enjoy!







No comments:
Post a Comment
Note: Only a member of this blog may post a comment.